Security
The Đeman Difference: What Sets It Apart?

In today’s rapidly evolving digital world, standing out means more than just having a great product or service. It requires innovation, cultural awareness, and the ability to connect meaningfully with your audience. That’s where Đeman enters the picture a term that’s gaining recognition across multiple domains including technology, folklore, culinary traditions, and the arts. But what exactly is Đeman? And why is it being talked about in such diverse contexts?
Understanding Đeman: More Than Just a Word
The word Đeman is rooted in several traditions and fields, making it a unique intersection of modern technology and cultural legacy. Depending on the context, Đeman can mean a digital platform, a mythical figure, an art form, a culinary ingredient, or a personality trait.
1. Đeman in Technology: A Digital Transformation Suite
One of the most prominent modern uses of the word Đeman is in the technology and productivity space. Đeman, in this context, refers to a multi-functional digital platform that merges:
- Productivity tools (task management, calendar scheduling)
- Branding and content development
- Social media planning and analytics
- AI-powered optimization features
According to ManagementWorksMedia, Đeman is being promoted as a one-stop digital solution for freelancers, small businesses, and digital marketers. What sets this platform apart is its minimalist design, real-time analytics, and cross-channel integration, enabling users to manage content, communications, and campaigns from a single dashboard.
“Đeman simplifies your digital journey from content creation to audience engagement, all in one place.”
Its growing popularity indicates a shift in how modern entrepreneurs are managing their online presence leaning toward all-in-one platforms that reduce tool fatigue and increase workflow efficiency.
2. Đeman in Folklore: The Nature Guardian

Outside of the tech world, Đeman carries deep cultural significance in Eastern European and Slavic folklore. Here, Đeman is often depicted as a forest guardian or ancestral spirit, often dwelling in sacred groves or misty mountains.
In tales passed down through generations:
- The Đeman punishes those who disrespect nature.
- It blesses communities that honor the land and traditions.
- It serves as a bridge between the living and the spirit world.
Researchers in Slavic studies describe Đeman as a dual-natured figure both protector and punisher. This nuanced symbolism reflects a larger message about harmony between humans and their environment.
3. Đeman in the Performing Arts: A Vietnamese Fusion
In Vietnam, Đeman also refers to a traditional art form that merges:
- Classical music
- Storytelling
- Poetry
- Dance
This hybrid performance style is usually staged during cultural festivals and spiritual ceremonies. The Đeman performance is characterized by:
- Use of traditional instruments like the đàn tranh and bamboo flute
- Graceful movements that tell age-old love or war stories
- Costume designs rooted in regional folklore
Cultural institutions in Hanoi and Ho Chi Minh City have started to revive Đeman through youth performance troupes, preserving the practice for new generations.
4. Đeman in Culinary Traditions: The Fragrant Leaf
In Southeast Asian cuisine particularly Indonesian and Malaysian Đeman refers to a local bay leaf used in:
- Curries
- Stews
- Coconut milk-based dishes
This aromatic leaf offers a subtle citrus, clove, and eucalyptus flavor, elevating dishes with its unique fragrance. While similar to the Indian bay leaf (tejpatta), Đeman leaves are more delicate and are often removed before serving.
Beyond flavor, this herb is associated with:
- Hospitality rituals
- Digestive health
- Spiritual cleansing in some folk practices
Its presence in daily meals and ceremonies underlines the multi-dimensional role of Đeman in Southeast Asian life.
5. Đeman in Modern Slang: A Compliment for Graceful Behavior

Interestingly, in several modern dialects across Southeast Asia and parts of Eastern Europe, the word “Đeman” is also used as slang to describe someone who is poised, respectful, and well-mannered.
For example:
- “You handled that situation like a real Đeman.”
- “She’s such a Đeman calm, graceful, and strong.”
It’s a compliment with cultural undertones, pointing to a person who combines dignity, tradition, and wisdom.
Conclusion: Why the Đeman Difference Matters
What truly sets Đeman apart is its versatility. It’s not just a tech product or a myth it’s a symbol that bridges tradition and innovation, culture and utility, local and global values.
Whether you’re exploring productivity platforms, discovering world folklore, enjoying culinary heritage, or learning about traditional art forms, Đeman serves as a touchpoint for deeper connection and understanding.
Frequently Asked Questions (FAQs)
1. What is Đeman?
Đeman is a multi-contextual term referring to a digital platform, a mythical figure, a traditional art form, a culinary herb, or a personality trait, depending on the region and context.
2. Is Đeman a software tool?
Yes, in the tech world, Đeman is an all-in-one digital management platform designed for content creators, small businesses, and marketers.
3. Where does the folklore of Đeman originate?
The mythological version of Đeman originates in Slavic and Eastern European folklore, where it is seen as a guardian spirit of nature.
4. How is Đeman used in Vietnamese art?
In Vietnam, Đeman refers to a traditional performance art blending music, dance, poetry, and storytelling.
5. What is the culinary use of Đeman?
In Southeast Asian cooking, Đeman is an aromatic leaf used to flavor dishes like stews and curries.
6. Is Đeman a real person or fictional?
In folklore, Đeman is a fictional spirit or deity. However, in slang, it can describe a person with dignified or respectful behavior.
7. What makes Đeman software different from others?
Đeman software integrates branding, content scheduling, analytics, and team collaboration in one interface, unlike fragmented tools.
8. How do you pronounce Đeman?
It is usually pronounced as “DAY-mahn” or “DEH-mahn,” depending on the local dialect.
9. Is Đeman available globally?
The digital platform version of Đeman is increasingly being adopted globally, especially among remote teams and freelancers.
10. Can Đeman be used in spiritual or ceremonial practices?
Yes, both the culinary herb and the performance form of Đeman are used in various spiritual and cultural ceremonies in Southeast Asia.
Click for more amazing info. News MM
Security
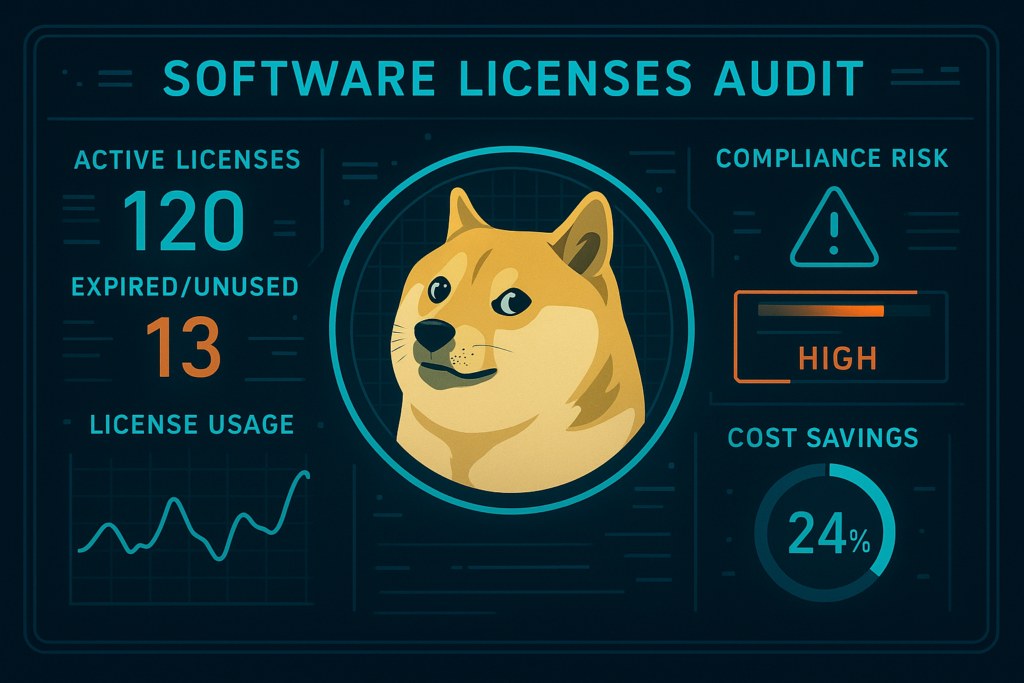
Doge Software Licenses Audit HUD: Simplify Compliance and Boost Efficiency

In today’s digital world, managing software licenses efficiently has become more important than ever. With government agencies and large organizations regularly dealing with multiple software licenses, it’s crucial to maintain compliance, optimize usage, and reduce unnecessary spending. One of the tools that has emerged to assist with this is the Doge Software Licenses Audit HUD. This tool helps simplify the process of managing software licenses and boosts operational efficiency, making it easier to stay compliant with legal and contractual obligations.
In this article, we’ll dive deep into what Doge Software Licenses Audit HUD is, its features, and how it can streamline the process of managing software licenses. We will also cover some key questions frequently asked about software license audits and provide you with a comprehensive understanding of how to optimize your software usage.
What Is Doge Software Licenses Audit HUD?
The Doge Software Licenses Audit HUD is a tool specifically designed to simplify the process of software license management and ensure compliance within government agencies and large enterprises. The HUD (Heads-Up Display) allows organizations to track software licenses, detect any discrepancies, and generate compliance reports to ensure that they are meeting legal and vendor requirements.
At its core, the Doge Software Licenses Audit HUD helps organizations avoid over-spending on software licenses they do not use, reduce the risk of non-compliance, and ensure that their software inventory is up to date. It’s a comprehensive tool that works across different platforms, integrates seamlessly with DevOps tools, and provides clear visibility into the license compliance status.
Key Features of Doge Software Licenses Audit HUD
1. Real-Time License Scanning
One of the most significant advantages of the Doge Software Licenses Audit HUD is its ability to perform real-time scanning of software licenses across an organization’s network. It can detect both open-source and proprietary software licenses within codebases, making it ideal for companies that have a mixed environment of commercial and open-source software.
2. Compliance Management
The HUD ensures that organizations stay compliant with their licensing agreements. It provides visibility into license types, counts, and compliance requirements. This feature is especially important for government organizations that need to adhere to strict licensing laws, such as those stipulated by the General Services Administration (GSA) or other regulatory bodies.
3. Detailed Reporting and Audit Trails
The tool generates detailed reports that document all software license usage, including any discrepancies, unused licenses, and the current compliance status. These reports are valuable during software audits, providing transparency and minimizing the risk of non-compliance. Additionally, the HUD maintains audit trails for every action taken, making it easier to trace any changes and resolve issues promptly.
4. Integration with DevOps Tools
The Doge Software Licenses Audit HUD integrates with popular DevOps tools such as GitHub, GitLab, and Jenkins. This integration allows for automated tracking and scanning of software licenses as code is being developed, which is a significant advantage for development teams working in fast-paced environments.
5. License Compatibility Matrix
This feature visualizes potential conflicts between software licenses. Many open-source licenses have restrictions on how they can be combined or redistributed, and the compatibility matrix helps organizations navigate these complexities. This reduces the risk of accidental violations that could lead to legal trouble.
6. Policy Enforcement
The tool can be configured to enforce organizational licensing policies automatically. For example, if an organization prefers certain software license types or restricts the use of particular vendors, the HUD will flag any deviations from these policies, making compliance enforcement more streamlined.
Benefits of Using Doge Software Licenses Audit HUD
1. Cost Optimization
One of the main benefits of the Doge Software Licenses Audit HUD is the ability to optimize software license costs. By identifying unused or underused software licenses, the HUD helps organizations eliminate wasteful spending. Companies often over-purchase licenses to avoid audit penalties or to ensure they have enough licenses for future growth, but this leads to unnecessary costs. The HUD allows businesses to purchase only what they need, thus improving budget allocation.
2. Minimized Risk of Non-Compliance
The risk of non-compliance is a serious concern for many organizations, particularly government agencies. Failure to comply with software licensing agreements can result in heavy fines and legal penalties. The Doge Software Licenses Audit HUD significantly minimizes this risk by keeping track of compliance requirements and ensuring that organizations are up-to-date with their licensing obligations.
3. Improved Productivity
With automated compliance tracking and real-time scanning, the Doge Software Licenses Audit HUD frees up valuable time for IT teams and software managers. Rather than manually tracking licenses and resolving compliance issues, teams can focus on higher-value tasks, such as development or strategic planning.
4. Streamlined Audits
Audits can be stressful and time-consuming, especially when there is no system in place to track license usage. The HUD simplifies this process by generating ready-to-go audit reports and ensuring that all required documentation is in place. This not only makes the audit process smoother but also reduces the time spent on preparing for external audits.
5. Better Decision-Making
With detailed data on software usage and license compliance, the HUD provides organizations with actionable insights. Decision-makers can use this information to make better choices regarding software procurement, policy changes, and vendor relationships.
How Does Doge Software Licenses Audit HUD Work?

The Doge Software Licenses Audit HUD works by scanning an organization’s software landscape and analyzing the licenses in use. Here’s a breakdown of the process:
- License Discovery: The HUD first discovers all software installed on the network and identifies the corresponding licenses associated with them. This includes both proprietary and open-source software.
- License Classification: Once the software is discovered, the HUD classifies the licenses into categories such as commercial, open-source, and government-issued software. This classification is essential for identifying potential conflicts and ensuring that the software is being used in compliance with its licensing terms.
- Compliance Check: The HUD then compares the current license usage against the terms of the agreement. It ensures that software is being used according to its license restrictions and that no violations have occurred.
- Reporting and Remediation: Finally, the HUD generates detailed reports that highlight any non-compliance or unused licenses. It also offers remediation suggestions, allowing the organization to take corrective actions before an official audit occurs.
Conclusion
The Doge Software Licenses Audit HUD is an essential tool for organizations looking to streamline their software license management. By simplifying compliance tracking, optimizing costs, and improving productivity, it provides immense value to businesses and government agencies alike. Whether you’re dealing with complex government regulations or managing a broad portfolio of software licenses, this tool helps ensure that you stay compliant while boosting operational efficiency.
Frequently Asked Questions (FAQs)
1. What is the Doge Software Licenses Audit HUD?
The Doge Software Licenses Audit HUD is a tool that helps organizations manage and track software licenses, ensuring compliance with licensing agreements and optimizing usage to reduce unnecessary costs.
2. How does the HUD help with compliance?
The HUD tracks software license usage, compares it against licensing agreements, and generates compliance reports, ensuring that organizations stay within legal and vendor requirements.
3. Can the Doge Software Licenses Audit HUD integrate with other tools?
Yes, it integrates with popular DevOps tools such as GitHub, GitLab, and Jenkins, making it easier to track licenses during software development.
4. How does the HUD improve cost efficiency?
The HUD identifies unused or underused licenses, allowing organizations to eliminate unnecessary spending and optimize their software license budgets.
5. Is the HUD only for government organizations?
While the HUD is designed with government organizations in mind, it can be used by any enterprise that needs to manage software licenses effectively.
6. What types of software licenses can the HUD track?
The HUD can track a variety of licenses, including commercial, open-source, and government-issued licenses.
7. How often should the HUD be used for license audits?
It is recommended to use the HUD regularly for real-time scanning and compliance checks to ensure ongoing license management.
8. Does the HUD provide detailed audit reports?
Yes, the HUD generates comprehensive audit reports that document software license usage and highlight any compliance issues.
9. Can the HUD help with resolving license conflicts?
Yes, the HUD’s license compatibility matrix helps organizations resolve conflicts between different software licenses.
10. How does the HUD ensure data security?
The HUD complies with industry standards for data security and ensures that all software usage data is protected and stored securely.
Click for more amazing info. News MM
Security
Is Your Internet Secure? The Story of 185.63.253.2pp and VPNs
First things first, it’s important to clarify that “185.63.253.2pp” isn’t a standard IP address. A valid IP address follows a specific format, typically four sets of numbers (like 192.168.1.1) ranging from 0 to 255, separated by dots. The “pp” at the end tells us that this isn’t a real, functioning IP address as it stands. However, we can use the numerical part, “185.63.253.2,” to explore the broader concepts of IP addresses, their significance, and how they relate to your online security. Think of the “2pp” as a placeholder for the bigger picture of internet security concerns we’re about to uncover.
What Exactly Is an IP Address?
Imagine sending a letter to a friend. You need their address for the letter to reach them, right? In the digital world, an IP (Internet Protocol) address works much the same way. It’s a unique numerical label assigned to every device connected to a computer network that uses the Internet Protocol for communication. This includes your computer, smartphone, tablet, and even smart devices in your home.
There are two main versions of IP addresses you’ll encounter: IPv4 and IPv6. IPv4 addresses, like our example “185.63.253.2,” consist of four sets of numbers. IPv6 addresses are much longer and use a combination of numbers and letters, designed to handle the ever-growing number of internet-connected devices.
Your IP address serves as a unique identifier for your device on the internet. When you visit a website, send an email, or stream a video, your device sends data packets that include your IP address as the “return address” so the destination server knows where to send information back. It’s how the internet knows where to deliver all those cat videos and online shopping deals!
IP addresses can be public or private. A public IP address is assigned by your Internet Service Provider (ISP) and is visible to the wider internet, allowing your devices to communicate with websites and servers worldwide. Private IP addresses, on the other hand, are used within your home or office network and aren’t directly accessible from the outside.
The Hidden Risks: How Your IP Address Can Compromise Your Privacy
While essential for internet communication, your IP address isn’t just a simple identifier; it carries a surprising amount of information about you, and this can pose significant privacy and security risks.
- Geolocation: Perhaps the most immediate piece of information your IP address reveals is your approximate geographical location. It won’t pinpoint your exact street address, but it can often tell someone your country, state, city, and even your ISP. This information, especially when combined with other publicly available data from your social media or online profiles, can lead to a more precise understanding of your whereabouts. For example, the IP address 185.63.253.2 is associated with Hostpalace Datacenters Ltd and is located in Lelystad, Flevoland, Netherlands. If this were your actual IP address, anyone looking it up could know you’re connecting from the Netherlands.
- Tracking Your Online Activity: Every website you visit, every app you use, logs your IP address. This allows websites to track your session activity, identify you as a returning visitor, and even tailor content or advertisements based on your location or Browse habits. While often used for legitimate purposes like personalizing your experience, this data can also be collected by third-party advertisers to build detailed profiles of your online behavior without your full awareness or consent.
- Target for Cyberattacks: Knowing your IP address can make you a potential target for cybercriminals.
- DDoS Attacks: Attackers can launch Distributed Denial of Service (DDoS) attacks, overwhelming your internet connection or network with a flood of traffic, causing it to slow down or even shut down completely.
- Vulnerability Exploitation: If a hacker knows your IP address, they can scan for open ports or vulnerabilities in your network devices (like your Wi-Fi router) or connected smart devices (IoT devices). This could allow them to gain unauthorized access to your network, plant malicious software, or even take control of your devices, turning them into part of a “botnet” for further illicit activities.
- Phishing and Impersonation: While an IP address alone won’t give away all your personal details, it can be used in conjunction with other information to craft more convincing phishing attacks or to impersonate you in online activities.
- ISP Monitoring: Your Internet Service Provider (ISP) has a record of your IP address and all your online activities linked to it. In some regions, ISPs are required to retain this data for a certain period, and in certain circumstances, they may be compelled to share it with law enforcement or other authorities. This means your Browse history is not entirely private from your ISP.
Enter the VPN: Your Digital Shield
This is where a Virtual Private Network, or VPN, comes to the rescue! A VPN acts like a secure, encrypted tunnel between your device and the internet. Instead of your internet traffic going directly from your device to a website, it first travels through the VPN server.
Here’s how a VPN protects your IP address and enhances your online security:
- IP Address Masking: When you connect to a VPN, your actual IP address is hidden, and you appear to be Browse from the IP address of the VPN server. So, if you’re in Pakistan and connect to a VPN server in the Netherlands, websites will see the VPN server’s IP address (for example, something different from 185.63.253.2, but still located in the Netherlands) and think you’re Browse from the Netherlands. This makes it incredibly difficult for websites, advertisers, or even your ISP to track your real location and online activities.
- Data Encryption: Beyond masking your IP address, a VPN encrypts all your internet traffic. This means that any data you send or receive – from your banking details to your emails – is scrambled into an unreadable format. Even if a cybercriminal somehow intercepts your data, they won’t be able to understand it without the encryption key. This is especially crucial when using public Wi-Fi networks, which are often unsecured and ripe for eavesdropping.
- Bypassing Geo-Restrictions: Because a VPN allows you to virtually change your location, it can help you access geo-restricted content. This means you might be able to watch streaming services or access websites that are only available in specific countries.
- Protection on Public Wi-Fi: Public Wi-Fi hotspots (in cafes, airports, hotels) are notorious for being insecure. Using a VPN on these networks creates a secure tunnel, protecting your data from malicious actors who might be trying to snoop on your activity.
- ISP Throttling Prevention: Sometimes, ISPs might intentionally slow down your internet speed (known as “throttling”) if you’re engaging in bandwidth-heavy activities like streaming or gaming. Since a VPN encrypts your traffic, your ISP can’t see what you’re doing, making it harder for them to selectively throttle your connection.
How to Choose a Reliable VPN Service
With so many VPN providers out there, choosing the right one can feel a bit overwhelming. Here are some key factors to consider:
- No-Logs Policy: This is crucial. A reputable VPN provider should have a strict “no-logs” policy, meaning they don’t record your online activities. Look for providers that have had their no-logs policy independently audited.
- Strong Encryption: Ensure the VPN uses strong encryption standards like AES-256, which is considered military-grade.
- Server Network: A good VPN will have a wide network of servers in many different countries. This gives you more options for masking your location and potentially better connection speeds.
- Speed and Performance: While all VPNs will slightly impact your internet speed due to encryption, a good VPN will minimize this impact. Look for reviews that mention speed and reliability.
- Ease of Use: The VPN app should be user-friendly and easy to set up on all your devices.
- Customer Support: Reliable customer support is important in case you encounter any issues.
- Simultaneous Connections: Check if the VPN allows you to connect multiple devices at the same time with a single subscription.
- Jurisdiction: Consider the country where the VPN provider is based. Some countries have stricter data retention laws than others.
Frequently Asked Questions (FAQs)
- What is the main difference between an IP address and a VPN? An IP address is like your device’s unique street address on the internet, allowing data to find its way to you. A VPN, on the other hand, is a service that masks this address and encrypts your internet traffic, providing a layer of privacy and security.
- Can my ISP see what I’m doing if I use a VPN? No, if you’re using a reliable VPN with strong encryption, your ISP will only see that you’re connected to the VPN server, but they won’t be able to see the specific websites you visit or the data you transmit. Your traffic will appear as encrypted data passing through the VPN.
- Is it legal to use a VPN? In most countries, using a VPN is perfectly legal. However, it’s important to remember that using a VPN to engage in illegal activities remains illegal. Some countries with strict internet censorship may restrict or ban VPN usage, so it’s always wise to check local laws if you’re traveling.
- Will a VPN slow down my internet speed? A VPN can slightly reduce your internet speed due to the encryption process and the extra distance your data travels to the VPN server. However, a good VPN service will minimize this impact, and in some cases, it can even help prevent ISP throttling, leading to a smoother experience.
- Are free VPNs safe to use? While tempting, many free VPNs can compromise your privacy and security. They might collect and sell your data, display intrusive ads, or have weaker encryption. It’s generally recommended to use a reputable paid VPN service for robust protection.
- Can a VPN protect me from all online threats? While a VPN significantly enhances your online privacy and security, it’s not a magic bullet for all threats. It protects your IP address and encrypts your traffic, but it won’t protect you from phishing scams, malware downloaded through malicious links, or revealing too much personal information on social media. A VPN is part of a broader online security strategy.
- How do I know if my VPN is working? You can check if your VPN is working by looking up your IP address before and after connecting to the VPN. There are many “What’s my IP?” websites available online. If your IP address changes to one associated with the VPN server’s location, then it’s working correctly.
- Can I use a VPN on multiple devices? Most reputable VPN providers offer the ability to connect multiple devices (computers, smartphones, tablets, smart TVs) simultaneously with a single subscription. Check the provider’s terms for the exact number of allowed connections.
- What’s the difference between a VPN and a proxy? Both VPNs and proxies can mask your IP address. However, a VPN encrypts all your internet traffic, providing comprehensive security and privacy for your entire device. A proxy typically only reroutes traffic for specific applications (like your web browser) and often doesn’t offer encryption, making it less secure.
- Should I keep my VPN on all the time? For maximum privacy and security, it’s generally recommended to keep your VPN on whenever you’re connected to the internet, especially when using public Wi-Fi. The slight impact on speed is often a small price to pay for enhanced protection.
The Bottom Line: Taking Control of Your Online Journey
While the specific IP address “185.63.253.2pp” might not be real, the concerns it raises about internet security and privacy are very much so. In an age where our digital footprint is constantly expanding, understanding how our online presence is tracked and what tools are available to protect it is essential.
Click for more amazing info. News MM
Security
ioFbodies.com Privacy: What You Need to Know

In today’s interconnected world, where our lives increasingly unfold online, understanding how our personal information is handled has become paramount. Every click, every purchase, and every interaction leaves a digital footprint, making privacy policies more than just legal jargon—they’re a crucial guide to how our data is managed. When it comes to platforms like ioFbodies.com, which likely deals with personal details such as names, addresses, and payment information, a robust and transparent privacy policy isn’t just good practice; it’s a fundamental commitment to user trust and security.
The Foundation of Trust: What ioFbodies.com Collects
At the heart of any privacy discussion is the question of what information a platform gathers. ioFbodies.com operates on a principle of data minimization, meaning they only collect data that is absolutely necessary to provide their services and enhance your experience. This isn’t about collecting everything they can, but rather focusing on what’s essential for their core functionalities.
When you interact with ioFbodies.com, whether by signing up for an account, making a purchase, or simply Browse, certain types of data are typically collected. This often includes:
- Personal Identifiable Information (PII): This encompasses details like your name, email address, and shipping address. This information is crucial for processing orders, communicating with you about your account, and ensuring products reach your doorstep.
- Contact Information: Beyond just email for order confirmations, this might include phone numbers for delivery updates or customer service inquiries.
- Payment Information: When you make a purchase, payment details are processed. However, it’s important to note that reputable platforms like ioFbodies.com typically do not store sensitive credit card numbers directly on their servers. Instead, they rely on secure, encrypted payment gateways that handle this information securely.
- Device Data: This refers to technical information about the device you use to access the website, such as your IP address, browser type, operating system, and unique device identifiers. This data helps ioFbodies.com optimize their website for different devices, troubleshoot issues, and understand general user behavior patterns (without identifying individuals).
- Usage Data: This includes information about how you interact with the website, such as the pages you visit, the products you view, and the time spent on various sections. This aggregated data helps them understand popular content, identify areas for improvement, and personalize your experience.
The collection of this data is primarily triggered by user actions, such as when you voluntarily provide information by signing up for an account or initiating a transaction. ioFbodies.com ensures that any sensitive data collected, such as payment details, is handled with the utmost care and through secure, encrypted channels to significantly minimize any associated risks.
Putting Data to Work: How ioFbodies.com Uses Your Information

Once collected, your data serves specific purposes, all aimed at enhancing your experience and ensuring the smooth operation of ioFbodies.com. Their approach to data usage is directly tied to the services they provide, focusing on transparency and value.
The primary ways ioFbodies.com utilizes the data they collect include:
- Order Processing and Fulfillment: This is perhaps the most straightforward use. Your name, shipping address, and payment information are essential for processing your purchases, arranging shipping, and delivering products to you efficiently.
- Customer Support and Communication: When you have questions, encounter issues, or require assistance, your contact information allows ioFbodies.com’s support team to reach out, resolve problems, and provide timely updates regarding your orders or inquiries.
- Website Improvement and Personalization: By analyzing aggregated usage and device data, ioFbodies.com can identify trends, understand user preferences, and make informed decisions about website design, functionality, and content. This helps them create a more intuitive and enjoyable Browse experience tailored to their users. This might involve suggesting products you might like based on your Browse history or showing you relevant content.
- Marketing and Promotional Activities (with consent): With your explicit consent, ioFbodies.com may use your email address to send you updates about new products, special offers, or relevant news. It’s crucial to note that this is always opt-in, meaning you have control over whether you receive such communications, and you can withdraw your consent at any time.
- Security and Fraud Prevention: Your data plays a vital role in maintaining the security and integrity of the platform. By monitoring usage patterns and device data, ioFbodies.com can identify and prevent fraudulent activities, protecting both their platform and their users from potential threats.
- Legal Compliance: Like any reputable online platform, ioFbodies.com must comply with various legal obligations. Your data may be used to fulfill these requirements, such as maintaining transaction records for tax purposes or responding to legitimate legal requests.
In essence, every piece of data collected by ioFbodies.com serves a clear, justifiable purpose, contributing to a seamless, secure, and personalized user experience.
Collaborative Ecosystem: Third-Party Sharing and Partnerships

In today’s digital landscape, very few online platforms operate in isolation. To deliver a full range of services, collaborations with specialized third-party entities are often necessary. ioFbodies.com acknowledges this reality and maintains a strict policy regarding the sharing of user data with these partners.
When ioFbodies.com engages with third parties, it’s always with a focus on enhancing the services they provide to you. These partnerships typically involve entities critical to their operations, such as:
- Payment Processors: These are specialized companies that securely handle credit card transactions and other forms of digital payments. When you make a purchase, your payment information is transmitted directly to these secure processors, which are responsible for the financial transaction. ioFbodies.com itself typically does not store your full payment card details.
- Shipping Companies and Logistics Providers: To ensure your orders reach you efficiently, ioFbodies.com shares necessary shipping information (like your name and address) with couriers and logistics partners. This enables them to deliver your packages promptly.
- Analytics Providers: Companies like Google Analytics may be used to help ioFbodies.com understand website traffic and user behavior in an aggregated, anonymized way. This data helps them improve their services without identifying individual users.
- Marketing and Advertising Partners: If you have given explicit consent, ioFbodies.com might work with marketing platforms to deliver relevant advertisements or promotional content. However, this is always done in a way that respects your privacy and consent preferences.
A cornerstone of ioFbodies.com’s third-party sharing policy is the emphasis on minimal data sharing and strict confidentiality agreements. This means:
- Only necessary data is shared: Partners only receive the specific pieces of information absolutely required to perform their designated function.
- Confidentiality agreements: All third-party partners are bound by rigorous confidentiality agreements that prohibit them from using your data for any purpose other than what’s specified by ioFbodies.com.
- Security standards: ioFbodies.com ensures that its partners maintain high security standards, similar to their own, to protect your data.
This approach ensures that while necessary collaborations occur, your personal information remains protected and its use strictly controlled.
Fortifying Your Data: Security Measures at ioFbodies.com
Data security is not an afterthought at ioFbodies.com; it’s a fundamental pillar of their operations. In an era of increasing cyber threats, proactive and robust security measures are paramount to safeguarding user information. ioFbodies.com employs a multi-layered approach to protect your data from unauthorized access, disclosure, alteration, and destruction.
Key security measures implemented by ioFbodies.com include:
- Data Encryption in Transit (HTTPS): When you interact with ioFbodies.com, all data transferred between your browser and their servers is encrypted using HTTPS (Hypertext Transfer Protocol Secure). This is indicated by the padlock icon in your browser’s address bar. HTTPS encrypts communication, making it unreadable to anyone trying to intercept it, thus protecting your information during transmission, such as when you submit login credentials or payment details.
- Encrypted Databases for Stored Information: Data stored on ioFbodies.com’s servers, including personal information, is protected through encryption. This means that even if a breach were to occur, the data would be unreadable without the appropriate decryption keys, significantly reducing the risk of sensitive information being compromised.
- Strict Access Controls: Access to user data within ioFbodies.com’s internal systems is tightly controlled. Only authorized personnel with a legitimate need to access specific information for their job functions are granted access. This principle of least privilege minimizes the risk of internal misuse or unauthorized viewing of data.
- Regular Security Audits and Vulnerability Assessments: ioFbodies.com routinely conducts security audits, vulnerability assessments, and penetration testing. These proactive measures help identify and address potential weaknesses in their systems before they can be exploited by malicious actors. This continuous vigilance ensures their security posture remains strong against evolving threats.
- Employee Training: All employees who handle user data receive comprehensive training on data privacy best practices and security protocols. This ensures a culture of security awareness throughout the organization.
- Incident Response Plan: In the unlikely event of a security incident, ioFbodies.com has a well-defined incident response plan in place to quickly detect, contain, and mitigate any potential breaches, minimizing their impact.
These comprehensive security measures reflect ioFbodies.com’s unwavering commitment to protecting your personal information and maintaining your trust.
The Lifecycle of Data: Retention and User Rights
Understanding how long your data is kept and the rights you have over it are crucial aspects of any transparent privacy policy. ioFbodies.com is committed to both responsible data retention and empowering users with control over their personal information.
Data Retention Policy
ioFbodies.com operates on the principle of data retention as long as necessary. This means:
- Purpose-Driven Retention: Your personal data is only retained for the period required to fulfill the purposes for which it was collected (e.g., to process your orders, maintain your account, or provide customer support).
- Legal and Regulatory Compliance: Data may also be retained for longer periods if required by law or to comply with regulatory obligations (e.g., tax records, financial transaction logs).
- Secure Deletion: Once your data is no longer needed for these purposes, ioFbodies.com ensures its secure deletion. This isn’t just about simple deletion; it involves methods that prevent data from being recovered.
- User-Initiated Deletion: Importantly, users can also request the deletion of their data at any time. This gives you direct control over your digital footprint on the platform.
Your Privacy Rights
ioFbodies.com recognizes and upholds a range of privacy rights, empowering you to manage your personal information effectively. These rights, often enshrined in major privacy laws, include:
- Right to Access (Request Copies of Your Data): You have the right to request and receive a copy of the personal data that ioFbodies.com holds about you. This allows you to understand what information is being collected and how it’s being used.
- Right to Rectification (Ask for Updates): If you believe that the personal data ioFbodies.com holds about you is inaccurate or incomplete, you have the right to request that it be corrected or updated.
- Right to Withdraw Consent (for Marketing): If you have previously given consent for marketing communications, you have the right to withdraw that consent at any time. This means you will no longer receive promotional emails or messages.
- Right to Erasure (Request Data Deletion): You have the right to request the deletion of your personal data under certain circumstances, for example, if the data is no longer necessary for the purposes for which it was collected, or if you withdraw your consent.
- Right to Restriction of Processing (Restrict Data Usage): In certain situations, you can request that ioFbodies.com restrict the processing of your data. This means that while your data might still be stored, it won’t be actively used for certain purposes.
- Right to Data Portability: This right allows you to receive your personal data in a structured, commonly used, and machine-readable format, and to transmit that data to another controller without hindrance.
To exercise any of these rights, ioFbodies.com typically provides clear instructions within their privacy policy or through dedicated contact channels, such as a privacy-focused email address.
Global Reach, Global Standards: Compliance with GDPR and CCPA
In an increasingly globalized digital world, adhering to diverse privacy regulations is a complex but essential task for any platform handling user data. ioFbodies.com demonstrates its commitment to high privacy standards by ensuring compliance with two of the most significant and influential privacy laws: the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
General Data Protection Regulation (GDPR)
The GDPR is a comprehensive data protection law enacted by the European Union (EU) that sets strict standards for how personal data is collected, processed, and stored for individuals within the EU and European Economic Area (EEA). Even if a company is not based in the EU, if it processes the data of EU residents, it must comply with GDPR.
ioFbodies.com’s adherence to GDPR means they uphold:
- Lawfulness, Fairness, and Transparency: Data processing must be lawful, fair, and transparent to the data subject.
- Purpose Limitation: Data is collected for specified, explicit, and legitimate purposes and not further processed in a manner incompatible with those purposes.
- Data Minimization: Only adequate, relevant, and limited data necessary for the purpose is collected.
- Accuracy: Personal data must be accurate and kept up to date.
- Storage Limitation: Data is kept no longer than necessary.
- Integrity and Confidentiality: Data is processed in a manner that ensures appropriate security.
- Accountability: ioFbodies.com demonstrates compliance with these principles.
Furthermore, for cross-border data transfers involving EU residents, ioFbodies.com utilizes legal mechanisms such as Standard Contractual Clauses (SCCs). These are pre-approved model clauses by the European Commission that provide appropriate safeguards for personal data when it is transferred outside the EEA to countries that do not have equivalent data protection laws.
California Consumer Privacy Act (CCPA)
The CCPA is a landmark privacy law in the United States, granting California residents extensive rights regarding their personal information. Similar to GDPR, it focuses on transparency and consumer control over data.
ioFbodies.com’s compliance with CCPA ensures that California residents benefit from rights such as:
- Right to Know: Consumers have the right to know what personal information is collected, used, shared, or sold.
- Right to Delete: Consumers can request the deletion of personal information collected about them.
- Right to Opt-Out: Consumers have the right to opt-out of the sale of their personal information.
- Right to Non-Discrimination: Businesses cannot discriminate against consumers who exercise their CCPA rights.
By aligning its practices with both GDPR and CCPA, ioFbodies.com demonstrates a robust commitment to global privacy standards, offering a high level of data protection to its users, regardless of their geographical location. This dedication to regulatory compliance instills greater trust and confidence in their handling of personal information.
Frequently Asked Questions (FAQs) About ioFbodies.com Privacy
Here are 10 frequently asked questions to help you better understand ioFbodies.com’s privacy practices:
- What types of personal information does ioFbodies.com collect? ioFbodies.com collects only necessary data such as names, email addresses, shipping information, and device data, primarily when you sign up or make purchases.
- How does ioFbodies.com use my collected data? Your data is used to support core functionalities like order processing, customer support, marketing (with your consent), and improving the website’s overall performance.
- Does ioFbodies.com share my data with third parties? Yes, ioFbodies.com partners with entities like payment processors and shipping companies. However, they ensure that shared data is minimal and governed by strict confidentiality agreements.
- What security measures does ioFbodies.com have in place to protect my data? ioFbodies.com uses data encryption (HTTPS) during transit and stores information in encrypted databases. They also have strict access controls for authorized personnel and conduct regular security audits.
- How long does ioFbodies.com retain my personal data? ioFbodies.com retains your personal data only as long as necessary to fulfill the purposes for which it was collected or to comply with legal obligations. They securely delete it when no longer required.
- Can I request that my data be deleted from ioFbodies.com? Yes, you have the right to request the deletion of your personal data at any time. Instructions for doing so are usually found in their privacy policy.
- What are my rights regarding my personal data on ioFbodies.com? You have several rights, including requesting copies of your data, asking for updates, withdrawing consent for marketing, requesting data deletion, and restricting data usage.
- Is ioFbodies.com compliant with GDPR? Yes, ioFbodies.com adheres to the General Data Protection Regulation (GDPR), ensuring compliance with strict regulatory standards for residents of the European Union.
- Is ioFbodies.com compliant with CCPA? Yes, ioFbodies.com complies with the California Consumer Privacy Act (CCPA), upholding the privacy rights of California residents.
- How does ioFbodies.com handle cross-border data transfers? For cross-border data transfers, especially concerning EU residents, ioFbodies.com uses legal mechanisms like Standard Contractual Clauses to ensure data remains protected.
Conclusion: Your Privacy, Their Priority
In an era where digital interactions are an integral part of daily life, ioFbodies.com stands out with its clear and robust commitment to user privacy. Their policy isn’t just a legal formality; it’s a foundational aspect of their operational philosophy. From the careful selection of data collected to its secure storage and the transparency with which it’s used, every step is designed to safeguard your information.
Click for more amazing info. News MM
-

 Celebrity10 months ago
Celebrity10 months agoIndia Rose Brittenham: All You Need to Know About Heather Thomas’ Daughter
-

 Celebrity10 months ago
Celebrity10 months agoMargot Rooker: All You Need to Know About Michael Rooker’s Wife
-

 Celebrity10 months ago
Celebrity10 months agoRobert Noah? All You Need to Know About Trevor Noah’s Father
-

 Celebrity10 months ago
Celebrity10 months agoNadia Farmiga? All You Need to Know About Taissa Farmiga’s Sister
-

 Celebrity10 months ago
Celebrity10 months agoJackie Witte? All You Need to Know About Paul Newman’s First Wife
-

 Celebrity10 months ago
Celebrity10 months agoCheryl Pistono? All You Need to Know About Kareem Abdul-Jabbar’s Ex-Girlfriend
-

 Celebrity9 months ago
Celebrity9 months agoWho is the Father of Jay-Z? Biography of Adnis Reeves
-

 Celebrity10 months ago
Celebrity10 months agoAbigail S. Koppel? All You Need to Know About Leslie Wexner’s Wife













